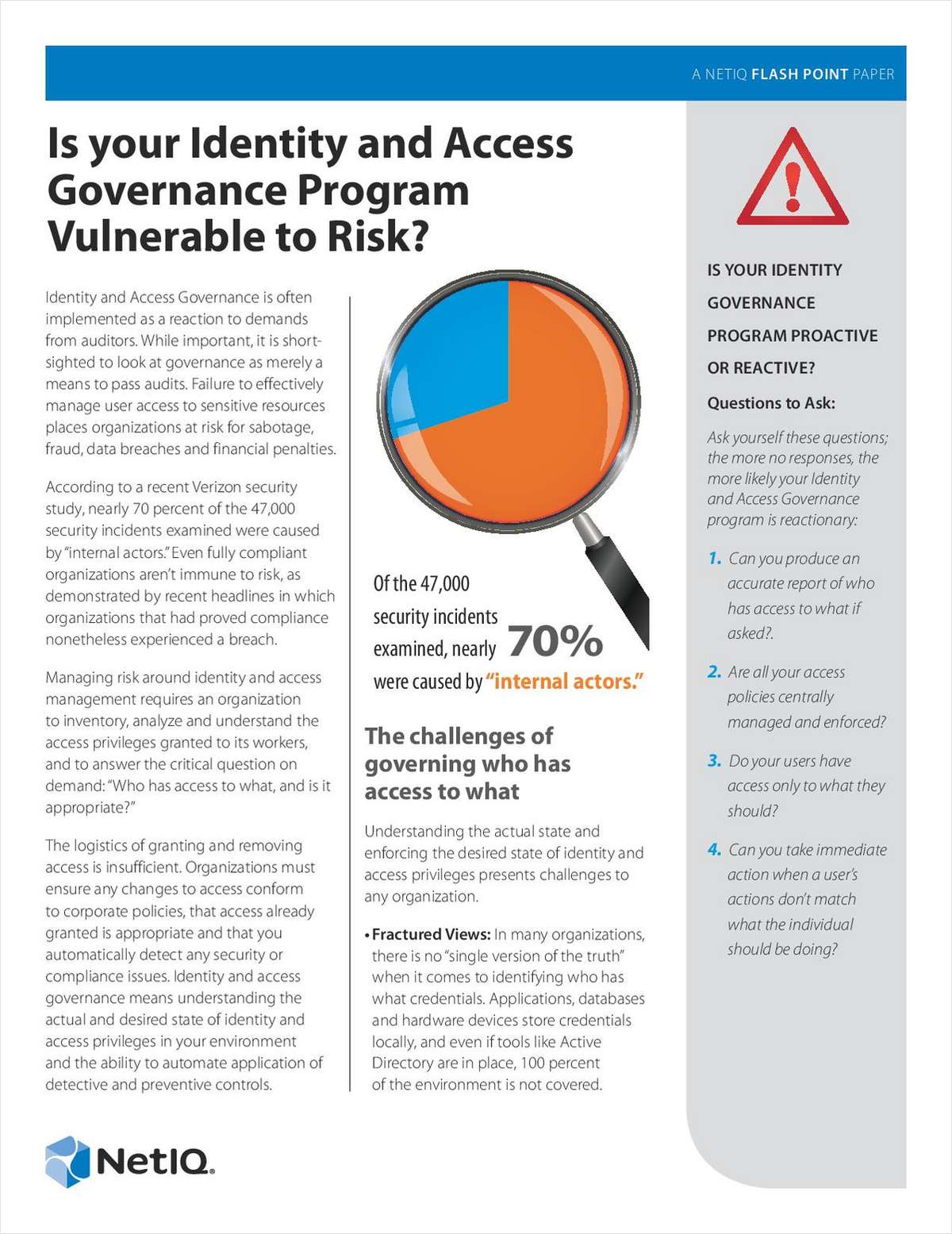
Is Your Identity and Access Governance Program Vulnerable to Risk?
Secure your business with comprehensive identity and access governance.
Your organization must inventory, analyze and understand the access privileges granted to its users to effectively manage risk. Proactive Identity and Access Governance (IAG) can help you answer the critical question: “Who has access to what, and is it appropriate?” NetIQ shows you how in this paper, which they’ve packed with:
- Questions to help you determine if your program is proactive or reactive
- Explanations of the challenges facing IAG programs
- Things to look for in an IAG solution