Defense Throughout the Vulnerability Lifecycle
New security threats are emerging all the time and defending against these risks is an ongoing battle. In response Security technologies available has also grown, making them harder to evaluate.
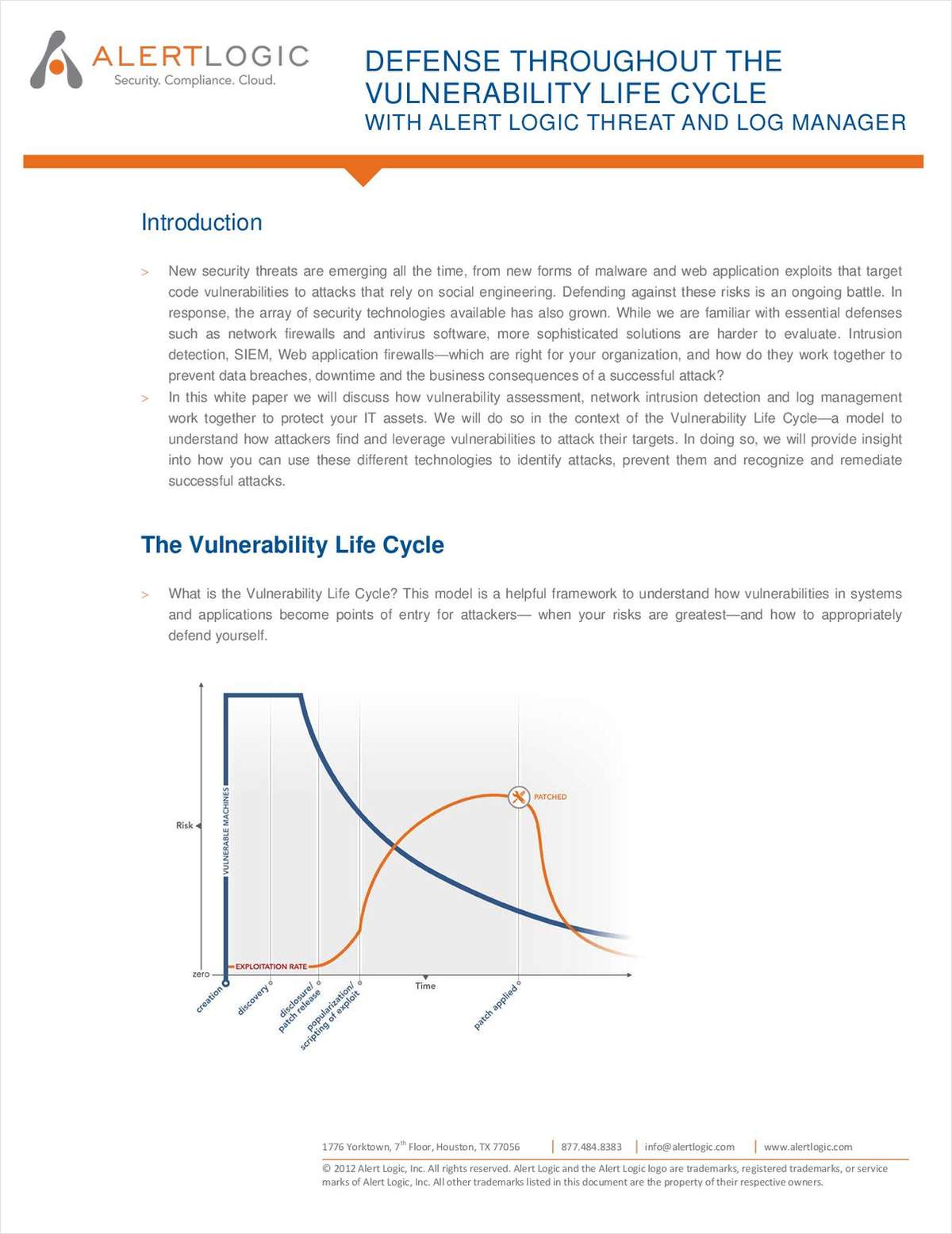
In this white paper – Defense Throughout the Vulnerability Lifecycle -here are three things you will learn:
- What the Vulnerability Lifecycle is
- How vulnerability assessment, network intrusion detection and log management work together to protect your IT assets
- How you can use these different technologies to identify and prevent attacks as well as remediate successful attacks




