How to Know If Your Identity and Access Governance Program Is Vulnerable to Risk
Learn whether your Identity Governance and Administration (IGA) program is proactive or reactive and what you can do to fix it.
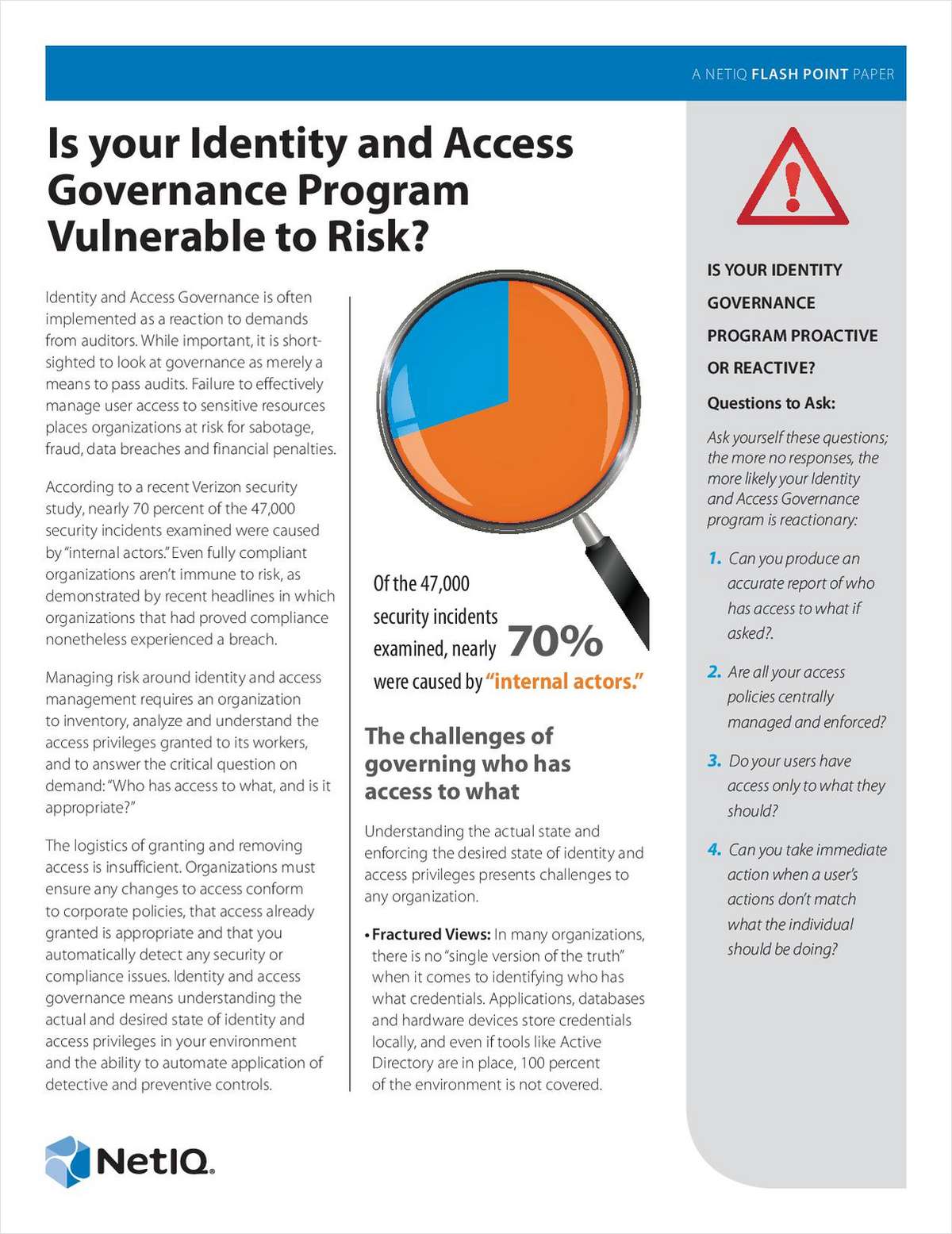
Many organizations implement IGA as a quick-fix to appease auditors and avoid fines. Such an ad-hoc approach can lead to poorly managed access, which in turn can create big security issues. Instead, a proactive IGA program that answers the question: “Who has access to what, and is it appropriate?” not only appeases auditors, it pleases the CIO by helping to prevent risk from insider attacks. Read this white paper to learn whether your IGA program is proactive or reactive.





